How To Detect Brute Force Attack Using Wireshark 35+ Pages Summary [1.2mb] - Updated 2021
55+ pages how to detect brute force attack using wireshark 1.8mb solution in PDF format . Explore the full course on Udemy special discount included in the link. Hover over Actions beneath the search bar and click View all Related Events. Brute force attacks are used for detecting login credentials using random combinations of username and passwords. Read also force and how to detect brute force attack using wireshark Then view or open the saved packet capture in wireshark and search for all traffic to and from the IP address of the camera ipaddr1234 for example.
To detect SSH brute force attempts on systems running systemd service manager CentOS7Fedora21RHEL7 you can use journalctl command with parameters. Brute-force attacks Brute-forcing is a method that tries a combination of numbers lowercase and uppercase letters and special characters to crack a password.

Pdf Investigating Brute Force Attack Patterns In Iot Work
| Title: Pdf Investigating Brute Force Attack Patterns In Iot Work How To Detect Brute Force Attack Using Wireshark |
| Format: Google Sheet |
| Number of Views: 8186+ times |
| Number of Pages: 55+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: July 2018 |
| Document Size: 5mb |
| Read Pdf Investigating Brute Force Attack Patterns In Iot Work |
 |
In the trends tab toolbar youll find the option to view anomalies.
So the attack must be carrying out either DoS or bruteforce. This section will demonstrate an SSH brute forcing attack that is NOT detected by Zeek. After passing this step the Wireshark application will appear as follows. 21You monitor the uplink for this particular network segment with your installation of Wireshark so that you can detect the attacker. This section was purposely put here to show the limitations of Zeek. Although research in this field has advanced considerably there still remain classes of attacks that are undetectable.

Security Onion Detecting A Brute Force Attack
| Title: Security Onion Detecting A Brute Force Attack How To Detect Brute Force Attack Using Wireshark |
| Format: Doc |
| Number of Views: 4152+ times |
| Number of Pages: 286+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: January 2019 |
| Document Size: 1.8mb |
| Read Security Onion Detecting A Brute Force Attack |
 |
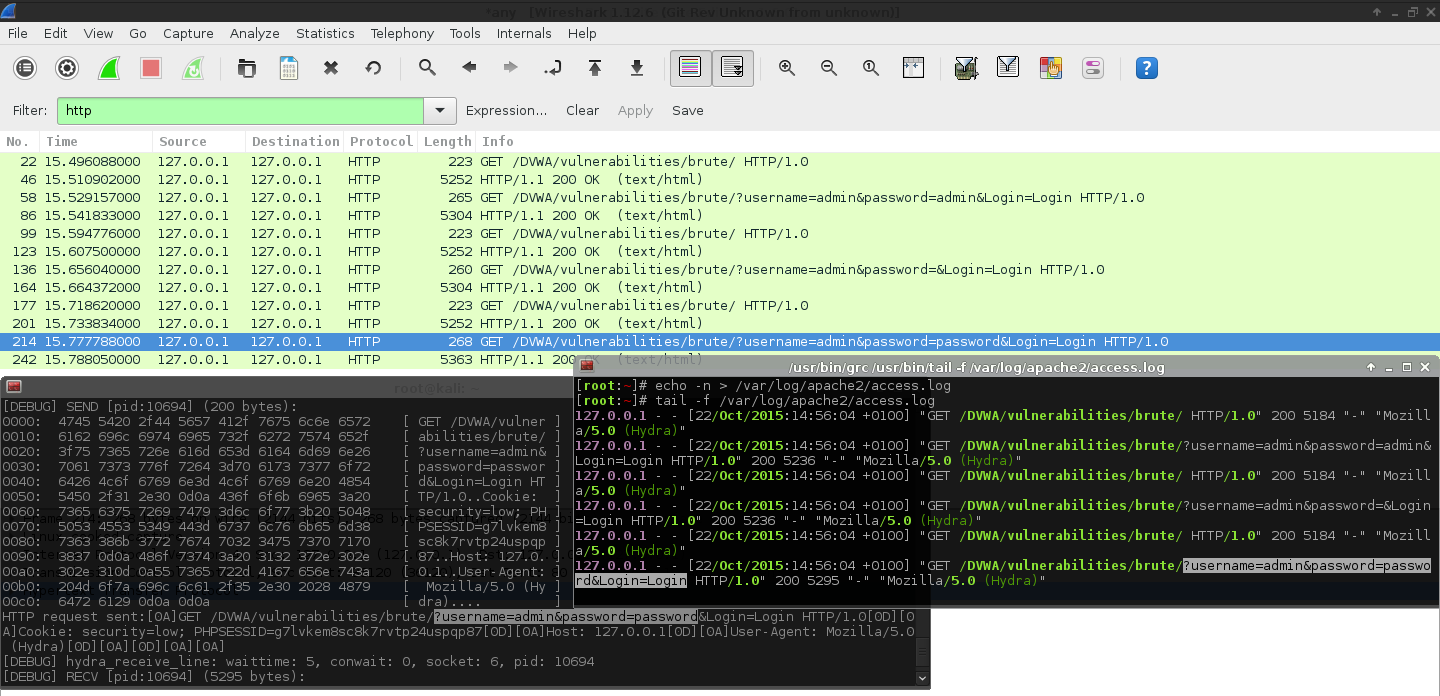
Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k
| Title: Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k How To Detect Brute Force Attack Using Wireshark |
| Format: Google Sheet |
| Number of Views: 3190+ times |
| Number of Pages: 203+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: April 2017 |
| Document Size: 1.6mb |
| Read Dvwa Brute Force Low Level Get Form Hydra Patator Burp G0tmi1k |
 |

How To Perform Brute Force Attack On Mysql Using Nmap Scripting Engine Nse Saraswati Repository
| Title: How To Perform Brute Force Attack On Mysql Using Nmap Scripting Engine Nse Saraswati Repository How To Detect Brute Force Attack Using Wireshark |
| Format: PDF |
| Number of Views: 9176+ times |
| Number of Pages: 148+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: November 2017 |
| Document Size: 810kb |
| Read How To Perform Brute Force Attack On Mysql Using Nmap Scripting Engine Nse Saraswati Repository |
 |
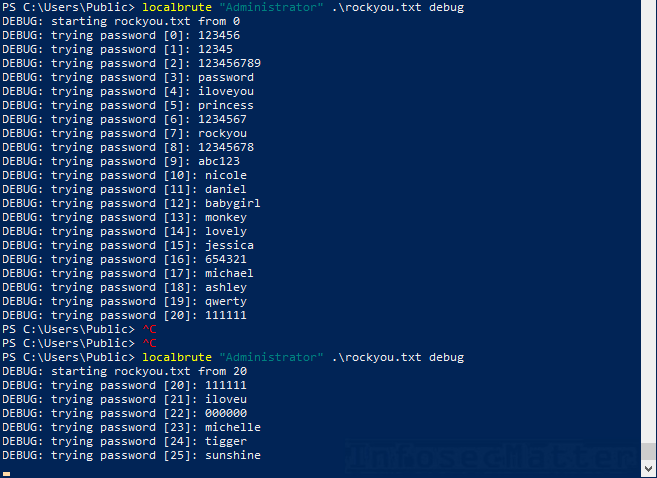
Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter
| Title: Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter How To Detect Brute Force Attack Using Wireshark |
| Format: Google Sheet |
| Number of Views: 8199+ times |
| Number of Pages: 265+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: January 2021 |
| Document Size: 1.1mb |
| Read Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
 |
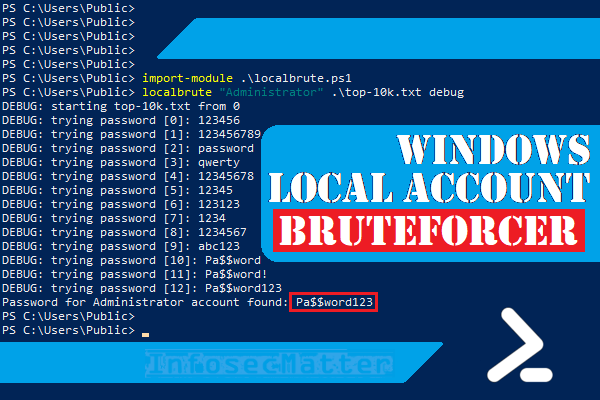
Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter
| Title: Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter How To Detect Brute Force Attack Using Wireshark |
| Format: Google Sheet |
| Number of Views: 3050+ times |
| Number of Pages: 213+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: October 2020 |
| Document Size: 3mb |
| Read Windows Local Admin Brute Force Attack Tool Localbrute Ps1 Infosecmatter |
 |

Brute Force Dictionary Attack Example Stack Overflow
| Title: Brute Force Dictionary Attack Example Stack Overflow How To Detect Brute Force Attack Using Wireshark |
| Format: Doc |
| Number of Views: 8180+ times |
| Number of Pages: 83+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: December 2020 |
| Document Size: 2.2mb |
| Read Brute Force Dictionary Attack Example Stack Overflow |
 |

Detect Password Cracking Attempts Wireshark Work Security
| Title: Detect Password Cracking Attempts Wireshark Work Security How To Detect Brute Force Attack Using Wireshark |
| Format: Google Sheet |
| Number of Views: 9167+ times |
| Number of Pages: 303+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: April 2019 |
| Document Size: 2.2mb |
| Read Detect Password Cracking Attempts Wireshark Work Security |
 |
Preventing Brute Force Attack Work Projects Work Simulation Tools
| Title: Preventing Brute Force Attack Work Projects Work Simulation Tools How To Detect Brute Force Attack Using Wireshark |
| Format: Google Sheet |
| Number of Views: 9188+ times |
| Number of Pages: 168+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: November 2017 |
| Document Size: 2.8mb |
| Read Preventing Brute Force Attack Work Projects Work Simulation Tools |
 |

Detect Brute Force Attacks Against Your Linux Servers Vps And Vpn
| Title: Detect Brute Force Attacks Against Your Linux Servers Vps And Vpn How To Detect Brute Force Attack Using Wireshark |
| Format: PDF |
| Number of Views: 7145+ times |
| Number of Pages: 234+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: May 2017 |
| Document Size: 1.4mb |
| Read Detect Brute Force Attacks Against Your Linux Servers Vps And Vpn |
 |
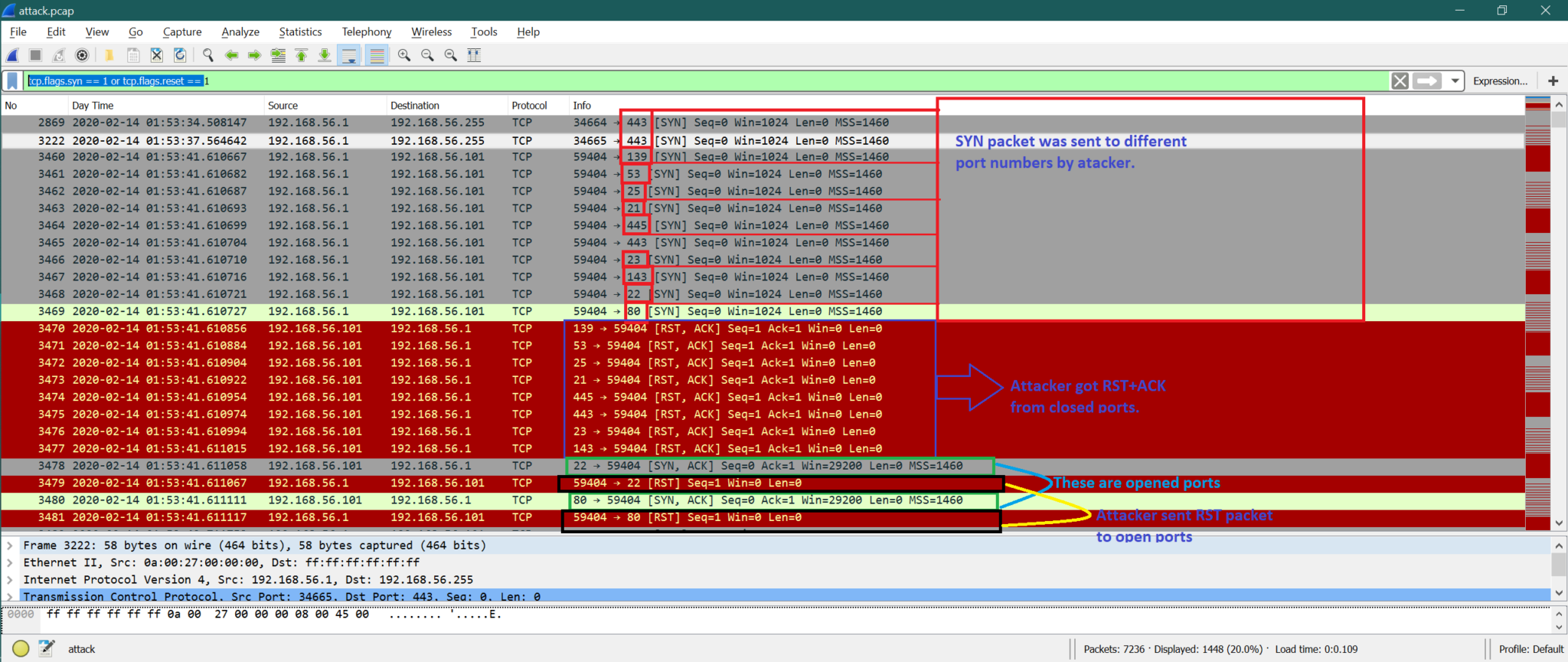
Wireshark Work Forensic Analysis Tutorial
| Title: Wireshark Work Forensic Analysis Tutorial How To Detect Brute Force Attack Using Wireshark |
| Format: PDF |
| Number of Views: 3240+ times |
| Number of Pages: 344+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: August 2018 |
| Document Size: 2.3mb |
| Read Wireshark Work Forensic Analysis Tutorial |
 |
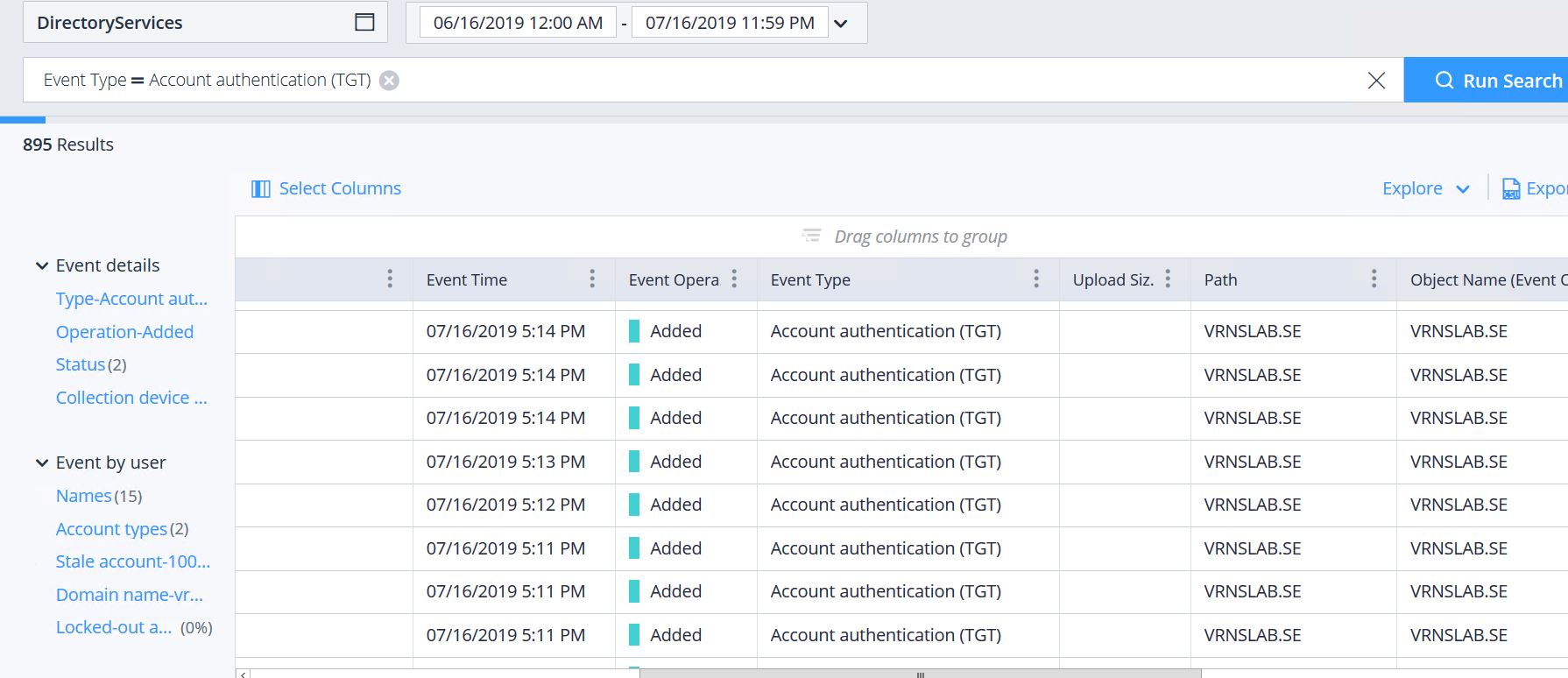
Bruteforce Attack Detection Through Ntlm With Varonis
| Title: Bruteforce Attack Detection Through Ntlm With Varonis How To Detect Brute Force Attack Using Wireshark |
| Format: Doc |
| Number of Views: 3470+ times |
| Number of Pages: 317+ pages about How To Detect Brute Force Attack Using Wireshark |
| Publication Date: January 2017 |
| Document Size: 1.5mb |
| Read Bruteforce Attack Detection Through Ntlm With Varonis |
 |
Look in Wireshark for unusual numbers of SSH login attempts whether or not they are successful. Therefore we know the attack is SSH-bruteforcing. This can be performed using certain tools such as Brutus THC Hydra Medusa Burp Suite intruder and many other tools available online.
Here is all you need to learn about how to detect brute force attack using wireshark When you choose your network card whose traffic you want to examine in this interface Wireshark will start showing you the packages. Although research in this field has advanced considerably there still remain classes of attacks that are undetectable. In this image youll see that there is an increase in 503 status codes. Using flow data for web applications promise detection noction using flow data for web applications promise detection noction windows local admin brute force attack tool localbrute ps1 infosecmatter security onion detecting a brute force attack pdf investigating brute force attack patterns in iot work how to perform brute force attack on mysql using nmap scripting engine nse saraswati repository bruteforce attack detection through ntlm with varonis detect brute force attacks against your linux servers vps and vpn The question explicitly states that the attacker has gained access.

Post a Comment
Post a Comment